
Get your FREE 30-day trial.
Please complete all fields.
Last year we introduced Salesforce Shield, a set of integrated services built natively into the Salesforce platform. Salesforce Shield raised the bar for customers with complex governance and compliance needs, empowering them to monitor and encrypt sensitive cloud data at rest—all with point and click tools.
Today, we’re excited to extend Salesforce Shield’s Platform Encryption service with Bring Your Own Encryption Key (BYOK) capability. This new feature, now in pilot, allows customers to generate and supply their own tenant secret to derive encryption keys, giving them increased ownership of data security.
With Salesforce Shield’s Platform Encryption built into our metadata platform, customers can encrypt data while preserving important business functionality, such as workflows, search and validation rules. And now, we’ve extended the same user-centric approach to BYOK, giving customers even more control over the encryption key lifecycle.
Shield Platform Encryption BYOK service extends our existing key management architecture via an API service, giving customers more control and flexibility to generate, manage and supply their tenant secrets. With this new service, customers now have two options to manage encryption key lifecycle: Salesforce's built-in key management infrastructure or leverage the new BYOK service to manage tenant secrets externally to Salesforce.
Our BYOK service gives customers the flexibility to use a variety of options for managing tenant secrets—from open source crypto libraries such as OpenSSL to their existing HSM [Hardware Security Module] infrastructure to a third-party service such as AWS Key Management Service or AWS CloudHSM. Additionally, Salesforce has partnered with leading third-party key brokering companies—including Vormetric —to further reduce the complexity, administration and governance efforts for managing the tenant secrets used to derive encryption keys.
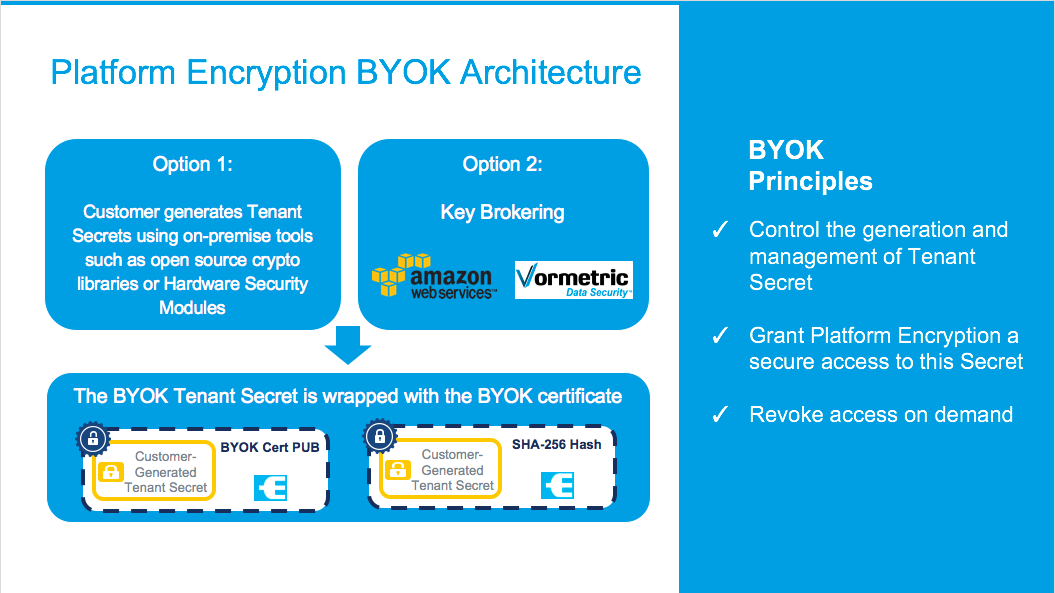
This approach to BYOK is unique in its balance of customer responsibility, industry compliance and ease of use—putting customers in the driver’s seat with the trusted assurance of Salesforce and 17 years of experience securing the public cloud.
In order to supply their own tenant secret, customers start by simply generating a secure certificate from Salesforce’s setup menu - in a declarative way. Customers can choose to generate either a self-signed or Certificate Authority signed certificate, depending on their own security and compliance requirements. The certificate’s private key is protected with an org-specific derived key in the HSM box, ensuring it can be only unwrapped by the HSM embedded within special purpose security hardware called a Key Derivation Server.
Customers then use that certificate’s public key to wrap their on-prem generated tenant secret before uploading it to Salesforce. This allows for a secure transport of keys back to our environment. The tenant secret is then paired with a master secret in Salesforce to derive the org-specific data encryption key used to encrypt sensitive data stored in standard and custom fields, files, and attachments. The derived keys are never persisted to disc ensuring maximum security for encryption keys.
Once a customer has supplied their tenant secret, they can use Platform Encryption as they normally would to strongly encrypt data at rest in Salesforce. Using BYOK, customers have the same flexibility to re-supply or destroy tenant secrets within both salesforce and their externalized key management service. Each time they supply a new tenant secret using BYOK, the data encryption key is rotated and that new key is derived and used to encrypt and decrypt data. This straightforward process allows customers to have both control and a greater role in managing keys, while reducing the burden of involved key management.
To learn more about Shield Platform Encryption, download this whitepaper.